Kernel Exploitation Part Four
This post is the fourth part of my notes from the lecture about kernel exploitation of pwn.college[0]. Read the previous post first:
Switching between rings
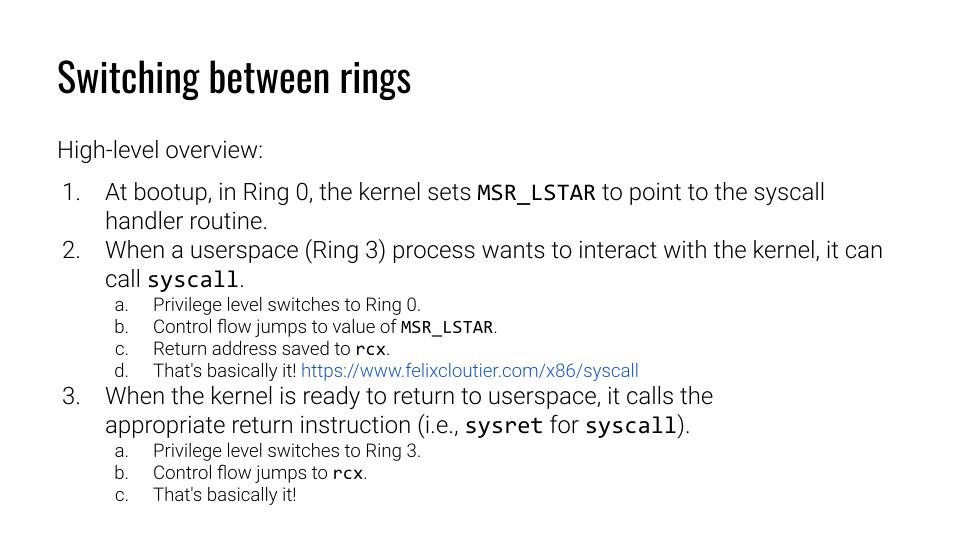
This slide made more sense after staring at it for a while. Because we started to define what rings are and how we are affected by them. Now, we want to know how such a switch occurs.
Any computer will boot with ring 0 enabled by default. I wrote about the boot process in my bachelor theses[1]. I did not write that detail. But it is safe to assume that the process is in real mode after power-up. It also includes that it is in ring 0. What is to remember here is that this is a historical aspect of CPUs. These things are part of the CPU that has to be present to ensure that nothing is breaking because it might be possible that SOMEONE still uses it! Intel can not afford this.
That reminded me of a different but similar problem within the industry, to stick to old working standards. Microsoft had vulnerabilities[3] that weren’t able to be fixed because it would break customer applications. Essential this was the reason why SMB v1 was kept for so long in windows until the NSA leak. Leading to the situation that even Windows 10 systems were being affected. Microsoft has disabled SMBv1 now. But there are more of such things in Windows and most likely in Intel too.
Obviously, we are not bothered with the boot process too much here. Once the kernel is loaded, we’re back into the course. Before I return to the lecture, I was wondering about that MSR_LSTAR .
After searching within the Linux kernel sources about it, I found this definition[2]. The value of MSR_LSTAR will be translated to 0xc0000082. Does that mean that written data are just dropped through into the register of the CPU? It is just a register? Somehow I feel stupid now because it did not make much sense until now.
Maybe…For instance, in some assembler code sample, there are using syscalls by writing into some special memory address. I think that is what is happening here as well. I guess that’s what he is implying within the video that everything is just the same, just a bit more special.
Ah, so your kernel sees that there is a pointer within the MSR_LSTAR register. That triggers the kernel to switch into ring 0. Then the CPU executes the code and once it completed it writes the return address into RCX.
Ah, so your kernel sees that there is a pointer within the MSR_LSTAR register. That triggers the kernel to switch into ring 0. Then the CPU executes the code until it finishes it.
Afterward, it will write the return address into RCX and will drop the privileges. This will be indicated by the keyword ‘CPL’. It resembles CPU Privilege Level in this context. Lastly the kernel will return the regular execution with the pointer stored in RCX.
Gosh I think I got it.
so far,
akendo
[0] https://pwn.college/modules/kernel
[1] https://blog.akendo.eu/post/2019.06.10-securing-hardware-with-coreboot/#boot-process
[2] https://github.com/torvalds/linux/search?q=MSR_LSTAR